A security bug, primarily focused on Intel CPUs at first, became well-known across the tech community over the last few days, with far-reaching concerns for security across swathes of chips, and affecting multiple manufacturers – not simply Intel alone. Intel, AMD, and Google have now all published official responses to the vulnerabilities, which are nicknamed Meltdown and Spectre.
Whatever your system, one of the best gaming keyboards wouldn’t go amiss.
Google’s Project Zero posted an in-depth analysis of their findings into the potential security bypass through speculated execution. This method allows a CPU to increase performance by guessing what needs to be done, before it is requested. Essentially, the bypass allows malevolent users to read system memory that should otherwise be entirely out of bounds, if they so wished to (and have the expertise).
There are three variants of these attacks outlined by Google. Variants one and two are nicknamed ‘Spectre’, and variant three is aptly named ‘Meltdown’ – which is Intel’s biggest bugbear currently. Meltdown can be fixed using page table isolation, a technique which may drastically affect performance in some situations for the worst – although possibly only for the time being.
AMD had previously commented on the situation through a Linux kernel patch, claiming that they were immune to attacks that the page table isolation patch blocked. Since then, AMD have posted an official response on the speculative execution vulnerability, summing up the potential threat to AMD processors across all three potential variants. Their findings, along with Google’s, point to a near-zero risk of variant two, and zero risk of variant three – i.e. Meltdown.
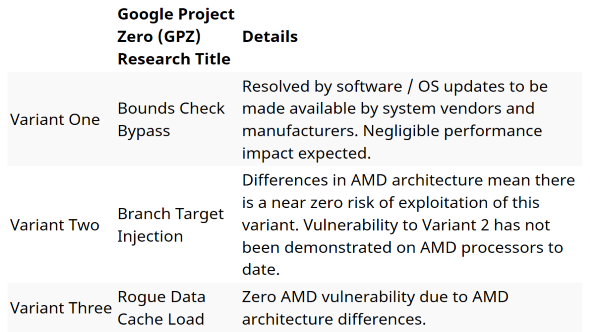
Variant one, however, will affect AMD CPUs. In fact, this vulnerability is a little tricky to patch, and actually will affect AMD, Intel, and ARM processors. The Spectre issues will supposedly need more than a little patch to fix, as the hardware itself will need to be changed in order to rectify the issue. This isn’t all bad news however, as the complex nature of the vulnerability also supposedly makes it difficult to use for an attack.
Software developers can attempt to mitigate the vulnerability themselves, with Mozilla and Google having already implemented fixes with their latest Firefox and Chrome builds, if required. AMD expect little performance impact as a result of any fixes, and it seems that the usual fare of good PC behaviour – such as keeping your applications up-to-date – will be more than enough to mitigate any potential threats to the average user.
Intel, however, have been a little more cryptic with their official response.
“Intel and other technology companies have been made aware of new security research describing software analysis methods that, when used for malicious purposes, have the potential to improperly gather sensitive data from computing devices that are operating as designed,” Intel write.
“Intel believes these exploits do not have the potential to corrupt, modify or delete data. Recent reports that these exploits are caused by a ‘bug’ or a ‘flaw’ and are unique to Intel products are incorrect. Based on the analysis to date, many types of computing devices – with many different vendors’ processors and operating systems – are susceptible to these exploits.”
Intel’s response has angered Linux creator, Linus Torvalds, who writes: “I think someone at Intel needs to really take a long hard look at their CPUs, and actually admit that they have issues.”

While Intel are quick to point fingers, they do, however, confirm that any performance impact for the average computer user should not be significant, and will be mitigated over time. The only users who should be worrying a little more are the huge data centres, with very specific workloads – such as Amazon, Google, and Microsoft – and it seems that they have been working together with Intel, AMD, and others on patching up this vulnerability for quite some time. They get paid to sweat the small stuff, anyways.
While the performance nerf is a little disconcerting for Intel users, the everyday impact to gamers is touted by Intel and AMD as almost negligible – although, these sources do have some vested interest in the matter. Patches are incoming for Windows users, which will at least nullify the Meltdown threat (and seemingly has little impact on performance), and general good PC practices, as outlined by both AMD and Intel, should be enough to grant you safe travels across the interwebs. Intel, AMD, ARM… whatever you got, you’ll likely be OK in the future.
