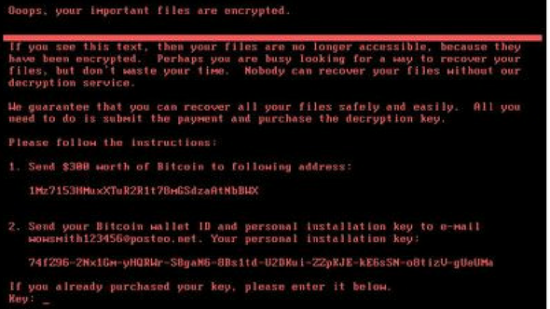
It seems that the MS17-010 exploit is continuing to inspire new and more insidious randomware. The latest goes by the names Petya, GoldenEye, NotPetya, and Petwrap, and like last month’s WannaCry attack it can spread to any non-patched computer using a Windows SMB sever bug.
You’ll be safe from viruses when downloading our list of the best free Steam games.
What’s new with Petya is that it will also look for cached network credentials and attempt to infect other computers via Windows Management Instrumentation. That means that even computers patched against the WannaCry exploit can be infected through the WMI vector.
Petya infections are commonly caused by Microsoft Office or Wordpad files that contain the ransomware. When you open the file and click the “Enable Content” button, Petya then runs itself and can spread through your PC and network with impunity.
If you’re infected by Petya, there’s not a lot you can do to restore OS functionality. The one thing that is imperiative, though, is to not let your PC reboot. During the reboot is when the Petya ransomware begins encrypting your files, and as long as you can prevent that you can use a Linux live CD or USB to recover and back up your files.
If you have not allowed Windows Updates to install in a while, you’ll want to make sure you do this immediately. Those it can’t absolutely prevent infection by Petya, it can close some attack vectors making it less likely it will make its way onto your system.
A thread on Reddit has also posted a possible vaccine that can keep Petya from taking over your PC via WMI. Modifying your Windows OS installation folder is something you’ll have to do at your own risk, but we haven’t seen any negative reports from anyone who followed the vaccination instructions.
For now, the best course of action is to treat any Microsoft Office or Wordpad files from sources you don’t trust 100% as if they’re infected. Also, strengthen your network security and lockdown your Windows Managment Instrumentation settings.